- Blog
- Announcements
- Worldcoin Foundation unveils new SMPC system, deletes old iris codes
Worldcoin Foundation unveils new SMPC system, deletes old iris codes
Applied research from the Worldcoin Foundation and TACEO, a team of cryptography engineers, has advanced the state of the art in biometric template protection and enabled the secure deletion of Worldcoin’s previous iris code system.
Working within a field of cryptography known as secure multi-party computation (SMPC), Worldcoin and TACEO have applied recent advances in SMPC for Machine Learning to iris codes, which enable Worldcoin to determine an individual’s uniqueness.
This new approach, which is open source and available in a Github repository, allows the iris codes to be individually encrypted into multiple different secret shares held by multiple parties. These parties can then work together to compute results over the secret information without learning anything about the secret itself.
With this, World ID has achieved an unprecedented level of privacy protection for deduplication (verification of uniqueness) of biometric templates. After the migration of iris codes to the new SMPC system, the previous uniqueness-checking system, including old iris codes, was securely deleted.
Introduction
Verified World ID users can prove that they are a unique human being without revealing who they are, unlocking new abilities in the digital realm such as collective protection from impersonation, deep fakes and influence campaigns. To achieve this, the system makes sure the user has not signed up before during sign up by applying the Daugman iris code method[1], which relies on the inherent uniqueness of irises.
Iris codes are unique and must be handled with the utmost care. Until recently, this meant using hardware security modules, encrypted drives and networks, identity and access management, etc. On top of this, World ID went much further through its additional layer of zero-knowledge proofs that allows an individual to use their World ID without revealing which World ID was used or who the user is.
Secure Multi-Party Computation
The best method to safely store critical data is a secret sharing scheme in which the secret is encrypted to a set of numbers called shares. These numbers individually are random and reveal nothing, but together their correlation contains the secret. The secret can only be recovered if all the shares are combined[2]—any fewer and nothing can be learned about the secret. You can imagine it as a combination safe with multiple dials where each participant only knows one of the combinations, or as the Horcruxes from the Harry Potter novels.

Secret sharing is like a safe with multiple dials where each participant only knows one code. Only if the participants work together can they open the safe and reveal the secret.
By distributing the shares over multiple trusted parties (participants), fault tolerance of security can be achieved. Even a complete security breach of some participants would not leak the secret, as long as at least one of the participants is still secure. Furthermore, this is one of the few results in cryptography that provides perfect secrecy, meaning it will always be secure regardless of which advances happen in, say, prime factorization and quantum computers.
Secret sharing is powerful, but on its own can only be used to store information. Often, we also want to do something with the information (i.e., run a computation over it). This is where Secure Multi-Party Computation (SMPC)[3] comes in. It allows the participants in a secret sharing scheme to work together and do a computation on secret information, while keeping that information secret. For example, suppose you and your colleagues want to know the average salary of your group, but none of you wants to reveal their own salary. To do this, each person creates secret shares of their salary and distributes the shares to their colleagues. Remember, these shares appear to be random numbers and do not reveal anything. Everyone then computes the average of the shares, which may seem nonsensical at first. But due to the so-called homomorphic property of the secret shares, the average of the shares is the same as a share of the average. Now that everyone has a share of the average, they can proceed to combine their shares to reveal the actual average value![4]





As an example of SMPC, consider three colleagues who earn $3K, $4K and $8K per month respectively. They want to know their average salary, but they do not want to reveal their own.
The colleagues decide to determine their average salary using a two-party SMPC with a simple additive secret sharing scheme. For this, the colleague who earns $3K per month creates random secret shares 7 and -4 which add to the secret value 3. The $4K per month colleague creates shares -5 and 9, and the $8K per month colleague creates shares 4 and 4.
Each colleague now distributes their shares to the two SMPC participants.
The first SMPC participant receives shares 7, -5 and 4 and computes the average, which is 2. The second receives shares -4, 9 and 4 and computes average, which is 3.
The two values 2 and 3 are secret shares of the answer. They are sent back to the colleagues who add them up to reveal the answer: 5
SMPC protocols have generally been too resource-intensive to run for large complex computations. This is why, despite their privacy protective qualities, they have not seen extensive use in biometric template protection. In a paper from August last year[5], a research team of the International Red Cross concluded:
“While SMC-Janus [an SMPC solution] offers the strongest data protection, its cost makes it unsuitable for large aid distribution projects.”
A recent line of work by Araki et al. (2016)[6], Mohassel and Rindal (2018)[7] and many others demonstrates powerful optimizations in SMPC protocols that make them efficient for machine learning problems. In joint work between the Worldcoin Foundation and TACEO, these methods have been adapted to create an SMPC protocol for comparing iris codes. This optimization makes it possible to apply SMPC to the problem of iris code uniqueness and achieves a speedup of more than 10,000×.
This allows iris codes to be encrypted as secret shares and distributed over multiple participants. Using the SMPC protocol, the participants can compare the iris code of a user signing up against the encrypted shares without ever having to decrypt the secrets. Once uniqueness is verified, the new user’s iris code is encrypted to secret shares and added. Unlike the previous state of the art, where the iris codes needed to be decrypted for each comparison, stored iris codes in the new multiparty system always remain encrypted and only the comparison distance result is revealed. Protocols designed to reveal even less in the future are currently being researched[8].
Implementation
The SMPC protocol is open source and available in a Github repository, and the implementation was audited by Least Authority. After entering production in March with the existing iris codes encrypted to secret shares, the SMPC protocol then ran concurrently with the previous system to verify reliability. In May 2024, the old system was shut down and securely deleted. Despite the breakthrough performance improvement, the new system requires 1152 cores, 3.6TB memory and uses 5 Gbps bandwidth across all parties.
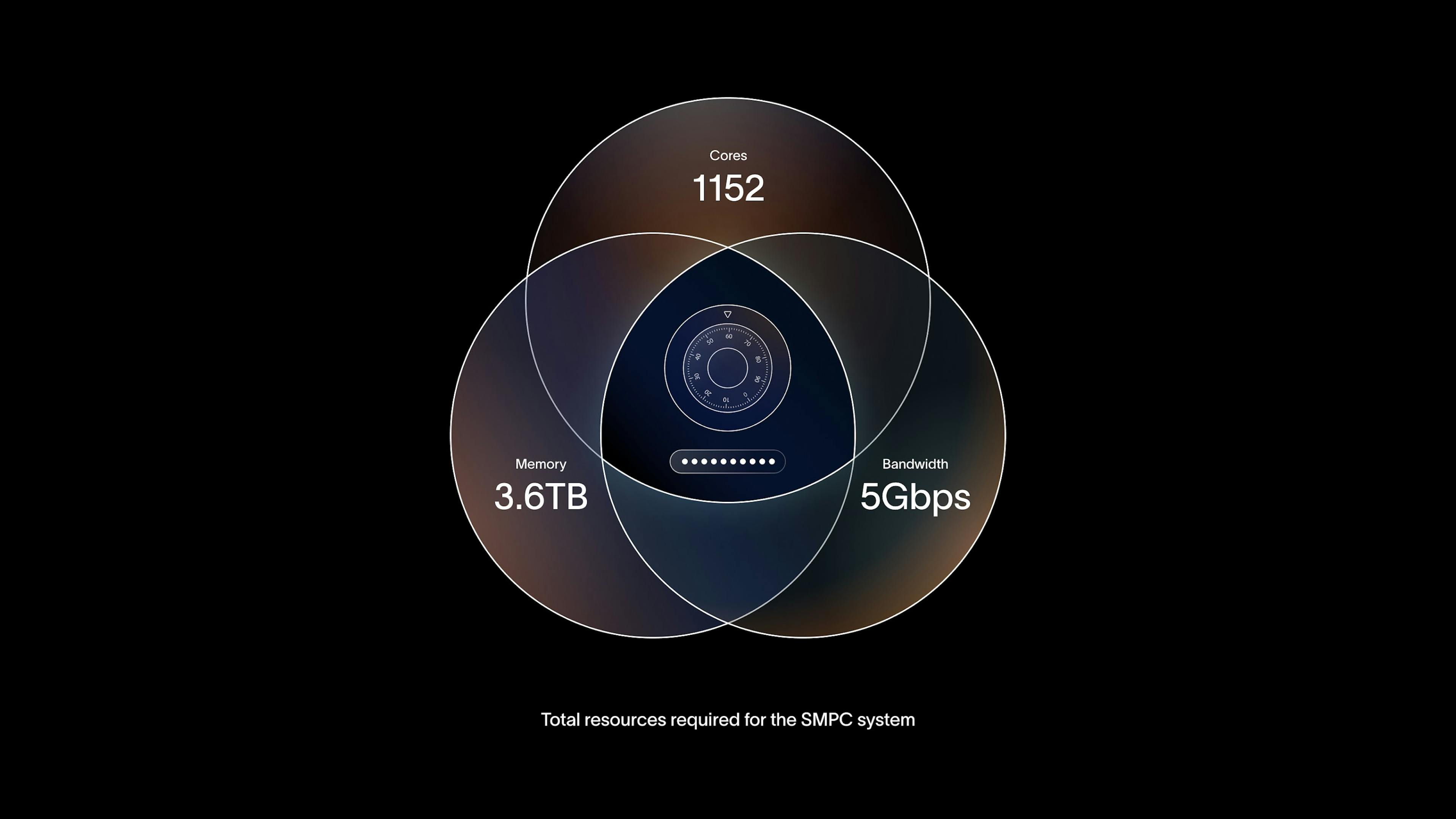
The new SMPC system requires 1152 cores, 3.6TB memory and uses 5 Gbps bandwidth across all parties.
The high priority of this workstream was reinforced after conversations with data protection authorities focused around further biometric template protection, particularly the Bavarian Data Protection Authority (“BayLDA”), the Worldcoin Foundation’s Lead Supervisory Authority in the EU.
As of writing, the participants of the current SMPC system are Tools for Humanity GmbH and the Worldcoin Foundation’s EU establishment. The Foundation is also currently in discussions with a number of other independent, third-party potential participants, including the Blockchain Center of the University of Zurich in Switzerland.
Why SMPC over other methods?
Before SMPC was explored in depth, a review of existing approaches to biometric template protection was conducted. Some methods, like fuzzy commitments and bloom filters, were ruled out because they do not provide cryptographic privacy. Instead they rely on introducing errors, which makes them unsuitable for checking uniqueness. Both homomorphic encryption (HE) and SMPC provide strong privacy, security and accuracy guarantees, but for the use case of uniqueness verification the security provided by SMPC is strictly better than HE. With the optimizations that were developed, the SMPC system also performs exceptionally well.
In addition to SMPC, in 2024 Worldcoin has implemented a series of privacy and security enhancing measures, along with increased user choice and control, including:
- Personal Custody to store personal information securely on a user’s device
- Unverify World ID to enable World ID holders to delete their iris code
- On-site age verification to further assure no underage World ID sign-ups
- John Daugmann (2004). How Iris Recognition Works. Pre-print.
- Secret sharing schemes can also be designed where the secret can be reconstructed with fewer than all shares, a so-called threshold amount. This is useful to protect against loss of shares. In the present version, we do not make use of a threshold and all shares are required.
- Ronald Cramer, Ivan Bjerre Damgård, Jesper Buus Nielsen (2015). Secure Multiparty Computation and Secret Sharing. Cambridge.
- Of course, one must always be wary of unintentional leakage in protocol design. For example, if there were two colleagues, each could easily compute the other's salary from the average and their own.
- Kasra EdalatNejad, Wouter Lueks, Justinas Sukaitis, Vincent Graf Narbel, Massimo Marelli, Carmela Troncoso (2023). Janus: Safe Biometric Deduplication for Humanitarian Aid Distribution. Pre-print.
- Toshinori Araki, Jun Furukawa, Yehuda Lindell, Ariel Nof, and Kazuma Ohara (2016) High-Throughput Semi-Honest Secure Three-Party Computation with an Honest Majority. Pre-print.
- Payman Mohassel and Peter Rindal (2018). ABY3: A Mixed Protocol Framework for Machine Learning. Pre-print.
- Remco Bloemen, Daniel Kales, Philipp Sippl, Roman Walch (2024). Large-Scale MPC: Scaling Private Iris Code Uniqueness Checks to Millions of Users. Pre-print.
The above content speaks only as of the date indicated. Further, it is subject to risks, uncertainties and assumptions, and so may be incorrect and may change without notice. A full disclaimer can be found in our Terms of Use and Important User Information can be found on our Risks page.